Tuesday, August 31, 2021
Here are the steps to install Eclipse:
1. Go to https://eclipse.org/downloads click on the "Download 64-bit" button
Monday, August 30, 2021
As a Linux administrator there will be times when you go in blind and do not know why system you are logging into, one way to CSI your way through the system is with the fd and fdisk command. Which will tell you who murdered Sideshow Bob. Not really it will just tell you the systems disk information and the partition it has. The first command you can run is the df command, if you run it by itself it would look a little cryptic. So most of the time you will see people run it with the -h option
The df command which is an abbreviation of the words disk free is a command used to display the amount of available disk space for file systems. It gives you amount of disk space available for each mount points.
The next command you can run is the fdisk command, as with df if you just type fdisk by itself, you won't get anything useful. So you usually see it with the -l option
fdisk gives you the disk partition information as you can see we have two partitions and mount points, the first is a boot partition which does not have a lot of space which it does not need a lot of space. The second partition has the bulk of space and is the system that we as users and administrators interact with. It also tells you the swap size and mount points. The home sector is also shown, you will often see the system administrator use this command when the system is running out of space.
Friday, August 27, 2021
SELECT UnitPrice, ProductName FROM Products ORDER BY UnitPrice DESC, ProductName
The query above sorts the results based on the most expensive products, and then the product name. Useful if you want a secondary sort criteria. For example if there are multiple products that are $14.00 then those products will be sorted by their names after the price has been sorted.
Thursday, August 26, 2021
SELECT FirstName + ' ' + LastName AS Employee, HireDate FROM Employees WHERE DATEPART(yyyy,HireDate) = 1994
Wednesday, August 25, 2021
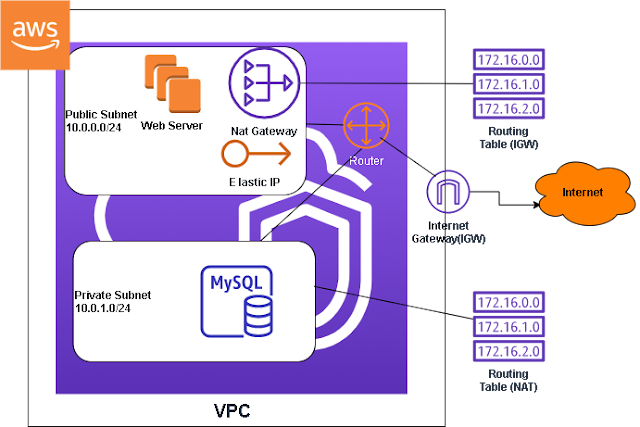
In most scenarios you don't want to expose all of your servers to be public facing. You probably want to configure your network so that only the server that is hosting your web application is public facing. What you want to do is put your web application on the public subnet and your backend servers on the private subnet. This private subnet can access the internet through a NAT gateway for software updates and other functions that require internet access. However, the outside world cannot establish a connection to servers in the private subnet. The NAT gateway resides in the public subnet, acting as a bridge between the public subnet and private subnet.
Tuesday, August 24, 2021
2. Under "Binary Distributions" select the last link
Monday, August 23, 2021
As a Linux administrator you can set the message of the day for users to see when they are logged in. It could be a reminder of a maintenance schedule or just to say high. Or if you want to get fired a fake hacked message...j/k...lol It does seemed like someone hacked your system sometimes when you see it as a user though.
The file that controls the Message of The Day message (pun) is located in /etc/motd
All you have to do is modify the file to display the message to the users in your system.
So vi /etc/motd and type in your message and the next time a user logs in he will see the message
One caveat is that it will only appear in text terminal session login such as logging in using Putty you will not see the message if you log in using the GUI.
Unfortunately, you've been told that you've been hacked by Kanya's evil twin brother, who's a better rapper!
Friday, August 20, 2021
<style>
a[href="https://www.google.com"]{font-weight: bold;font-size:200%;}
</style>
As an HTML creator you don't even need to worry about the markup, the selector automatically applies the styles once it finds the value. So the markup would be like this
<a href="https://www.google.com">google.com</a>
Thursday, August 19, 2021
SELECT AVG(UnitPrice) AS AveragePrice FROM Products
Wednesday, August 18, 2021
In the previous post we associated our Elastic IP with an instance directly. In this post we are going to take another approach to assign our Elastic IP to our instance. In this approach we will create an Elastic Network Interface and associate it with our instance instead. In the first approach the Elastic IP replaces the public IP because we associate it directly to the instance. But if we create an Elastic Network Interface we are essentially adding a second interface in our instance with two IPs, eth0 is the main network interface and eth1 will be the second interface. It's like having two network interface in the physical world but this time it's virtualized in AWS.
Here are the steps to create a network interface:
1. Create an Elastic IP, follow this post if you don't know how.
If you look at the instance description you will see that there's no Elastic IP address assignment, so if you stop and start the instance you will get a new public IP, and there's only one network interface (eth0). By the time we are finish with this post the instance will have tow network interfaces and an Elastic IP.
Tuesday, August 17, 2021
The first thing you want to do in Python is to install the latest version of Python. Even though most Linux and MAC distribution has Python installed by default, you still want to install the latest version of Python. The latest stable version of Python at the time of this writing is version 3.8.5 in this post we are going to install version 3.6.5 on our Linux instance.
1. Open up the terminal and type the following commands
sudo su
mkdir /opt/python
cd /opt/python/
wget https://www.python.org/ftp/python/3.8.5/Python-3.8.5.tgz
tar xzf Python-3.8.5.tgz
Monday, August 16, 2021
The init command is a useful command that allows you to put your Linux operating system into a system level based on a numbering system. It's useful when you want to put your system in other states besides shutdown and reboot. Kind of like the safe mode in Windows.
Here are the system levels (0-6):
- 0 Shutdown the system (init 0)
- 1 Single-user mode; can be alias with s or S (init 1 or init s or init S)
- 2 Multiuser mode without networking ( init 2)
- 3 Multiuser mode with networking (init 3)
- 4 Not used
- 5 Multiuser mode with networking (init 5)
- 6 Multiuser mode with networking and GUI ( init 6 )
To execute the command you simply type in the command in the terminal session as root
Friday, August 13, 2021
To apply a style to a class you define the class in the stylesheet as
.rainbow { color: pink; font-weight: bold; font-size:24px;}
Then you would use the class as such in the HTML markup
<p class="rainbow">What color am I?</p>
But if you want to apply style to an id that's used in HTML markup you have to do the opposite.
To reference an id in HTML you have to prefix your CSS style with the # character so in the CSS style you would have the following declaration
Thursday, August 12, 2021
- COUNT(*) count all the rows in the table including
- COUNT(column) return all the rows that contains value for the column, excluding the columns with null value
SELECT COUNT(*) AS NumberOfRows FROM Customers
Wednesday, August 11, 2021
When an instance is created in AWS a public and private IP is assigned to the instance. The private IP does not change, but the public IP address changes each time the instance reboot or is stopped. On reboot you might be lucky enough to grab the same public IP, but it's not guaranteed. But on stoppage you will definitely be assigned a new public IP.
That's probably not a good thing a real world situation, that's where an Elastic IP comes into play. An Elastic IP is a static IP that when assigned does not change. However, there's no free lunch so you will be charged for it. So only create one if you really need it. I would recommend that you use the public DNS instead when you are not in production. Say the development and test environment. You might want to spend some money on the staging environment to mirror production as close as possible.
In the following section I will show you how to create an Elastic IP and assign it to an instance. You probably want to delete it after you create it if you do not want to pay. Only keep it if you want to use it.
Tuesday, August 10, 2021
A Blockchain is a distributed network of containers with data, a hash, and a pointer to the previous hash. A hash is a text that consists of an input of all the parts of the block, and it will generate the same hash every time the input is the same. So if the block has been tampered with the hash will be different. On top of this there's a global record of the transaction that's distributed to everyone in the ecosystem. Making it almost impossible to to tamper with because if a hash has been tampered with there needs to be a consensus of the change before it is deemed valid. A consensus consists of 50% of the users.
If the hash, data, or anything of block 1 changes, the block 2 becomes invalid because block 1 will have a new hash and block 2 will be pointing to the wrong previous hash, making everything after it invalid, therefore it is in everybody's interest that changes are made very difficult because it would greatly impact the integrity of the blockchain. There are many checks and balances that must be met before a new block is accepted in the blockchain. Obviously there needs to be something that will correct a bad new block chain, else if a new block chain is bad then nobody can add a new chain to the blockchain anymore.
Monday, August 9, 2021
The most common way to troubleshoot a networking issue is to trace the sending and receiving of packages between hosts. Almost all OS has this kind of command and Linux is no exception. In Linux we use the traceroute command to trace the package from point A to point B.
To use the command you basically type the command traceroute and then the hostname for example if you want to trace the route to www.google.com you simply type traceroute www.google.com
If you don't have the command install you can install it by typing the following command dnf install traceroute -y
So now let's run the command traceroute www.google.com and see what happens
As you can see it starts with the gateway then each hop is labeled with a number. You can see when hops takes the longest and see the bottleneck in your network.
Friday, August 6, 2021
The possible media values are the following:
- all - all presentation media
- print - used for display print and print preview
- screen - all screens that uses the browser user agents
Wednesday, August 4, 2021
CloudWatch is a service on AWS that is used to monitor services on AWS via metrics. In addition to monitoring resources. CloudWatch can be used to set alarms and perform some actions on the instance when a certain condition is met. In this post we are going to set an alarm on our instance if CPU utilization gets to a certain threshold. Which is a typical safeguard that most environments have, there are several actions that you can take when the threshold is met, in our case we are going to terminate the instance if the CPU utilization reaches 75%.
The following shows you how to set a CloudWatch alarm on our Linux instance:
1. Click on "Monitoring" tab in the "Instances" page, then click on the "Create Alarm" button
Tuesday, August 3, 2021
In the last post we created our ACME Bank database in MySQL, the next step is to get the values from the Values table in the Asp.Net Core WebApi controller.
Let's create some test data so that we could retrieve the values from the database. The Values table could contain anything. So I am going to store famous philosophers throughout history. These philosophers are so famous that they only have one name:
You can run the SQL insert statement below to seed the data in MySQL:
INSERT INTO acmebank.Values (
Name
)
VALUES
(
'Socrate'
),
(
'Plato'
),
(
'Spock'
),
(
'Thanos'
);
So your Values table should look like this when you executed the insert query
Monday, August 2, 2021
In Linux there's a service often called the Central Logger which generates logs for itself or if permited collects logs for other servers. The service name is rsyslog and the configuration file is located in /etc/rsyslog.conf
One of the more common usage scenario is that once you scaled out your infrastructure and have hundreds of servers you don't want to log into every servers that are having problems if you need to troubleshoot an issue. That would take forever, so it is useful to have a centralize logging location.
The command to install the package is dnf install rsyslog -y
To start and enable the service you can type the command
- systemctl start rsyslog
- systemctl enable rsyslog
In the conf file /etc/rsyslog.conf there's a line that specifies the remote server to send you logging information to, if the server is going to be the client and not the central logger. Look for the line#
#'.' @@remote-host:514
If you want to send you logs to another server replace the remote-host with the host's IP address or fully qualified hostname and as you can see it will be sending traffic through port 514
Now you can run the service with the command systemctl start rsyslog